For any vacation rental company considering selling, there are many areas of preparation needed to realize a successful sales process. This article will discuss what types of technology-related data an owner should be prepared to provide based on the type of sale.
Technology in vacation rental companies ranges from simple to very complex, depending on the tools and solutions that are in use and the extent of digital transformation that has been completed.
For example, some VRMs have housekeepers using printed reports while others have a mobile application on their personal phones. A larger, geographically distributed company may have a wide area network connecting its systems while a smaller company may only provide wireless Internet access and leverage a software-as-a-service (SaaS) solution.
These examples can extend to all areas of operations in a VRM’s technology ecosystem. No two acquisitions are exactly the same, but there are common technology data requests depending on the sale type: contract buy (owner contracts/units), asset buy (stuff), or a stock purchase (company). One of the sticking points in a VR sale is the seller’s understanding of the technology systems involved. Frequently, VR owners do not have comprehensive documentation of the systems and assets that run the business.
The diligence an acquirer pursues will greatly impact his or her success in ongoing operations. In my experience, one deal included acquiring a proprietary system but not the add-on connector for distribution because it was not discovered or divulged in the diligence process.
Another purchase exposed the buyer to active network penetration and a resulting data breach because of a lack of focus on the current security in place. Failure to reveal a prior data breach resulted in fines that the buyer then had to recover from the seller in another deal. One website went dark for two days because it was not listed in the diligence data and lost connectivity to the PMS during system changes. Omissions can result in a financial loss to the seller, so it is important to provide all of the information available or requested.
Typical data requests in a diligence process are provided below. Depending on the size of the acquisition target and purchaser, the detail can be increased or flattened. Taking the time to develop this collection will prepare the target for a successful and productive engagement.
When an acquirer requests data from a target, the promptness and depth of the response signals a professional, well-run operation and provides confidence in the deal. While acquirers typically have a data request template, your prepared information can be easily pasted in or linked by reference. If there are questions that aren’t clear or understood, it is important to ask for clarification or help to ensure full transparency and data validity. It is important to note that this type of information should never be provided until a nondisclosure agreement has been executed. Deal brokers and consultants are available to help with this work, including data extraction and documentation if the seller wants assistance or needs to focus on other areas.
Contract Purchase Implications
In a contract purchase, the buyer typically does not need the current systems or technology services. The main focus is on the contracts and related data to be provided. Be ready to export data from your systems in a format the buyer can consume. The use of spreadsheets is common. Be sure to understand the scope of data the buyer will need and the date range. Two years of historical data is a common request.
Prepare a summary of all existing technology contracts to be used to terminate services no longer needed post sale. Plan to pay any early termination fees that may be required. Plan to maintain any systems or data needed to support any legal or financial reporting in the future, typically for three to seven years depending on the data type.
Asset Purchase Implications
For an asset purchase, the buyer purchases some or all of your assets, such as computers, websites, data circuits, and technology vendor contracts and services. In addition to these contract details, additional data related to the assets to be conveyed is needed. Compile accurate data for any assets or services to be transferred. Verify that existing agreements allow a transfer, and clearly detail any that have unique requirements for transferability.
Stock Purchase Implications
In a stock purchase, the buyer needs as much data as possible to sustain current operations and to support the staff, owners, and guests post sale. More detailed information about your technology ecosystem is needed to support the value and operations of the business. Collect all of your active technology-related contracts. These will include software systems (on-premise or SaaS); hardware support agreements; telecommunication products including voice, data, and cellular services; and any vendor support agreements.
The types of data needed are detailed below (but may not be fully comprehensive).
Tech Hardware
Computers, servers, network equipment, telephone systems, company cell phones with full detail of models, purchase date or age, and contract or warranty status. An inventory or all phone lines and data circuits should be included. A spreadsheet schedule is an easy way to track and share this information if no other asset inventory is available.
Software Systems
Include desktop software (Windows, Office, etc.), financial, HR systems, CRM, call center, PMS, housekeeping, maintenance, association management, collaboration tools, time tracking, payroll, point of sale, project management, website analytics tools, and source code of any proprietary systems. Be prepared to provide copies of all related contracts or proof of licenses, and verify the transferability of any that are needed.
Security Systems
These could include IT operating tools, antivirus software, firewalls, VPN, SFTP, application patching, and intrusion protection systems.
IT Support Structure
Provide current resource roles and reporting lines. If support is outsourced, supply the current agreement including the types of support it includes.
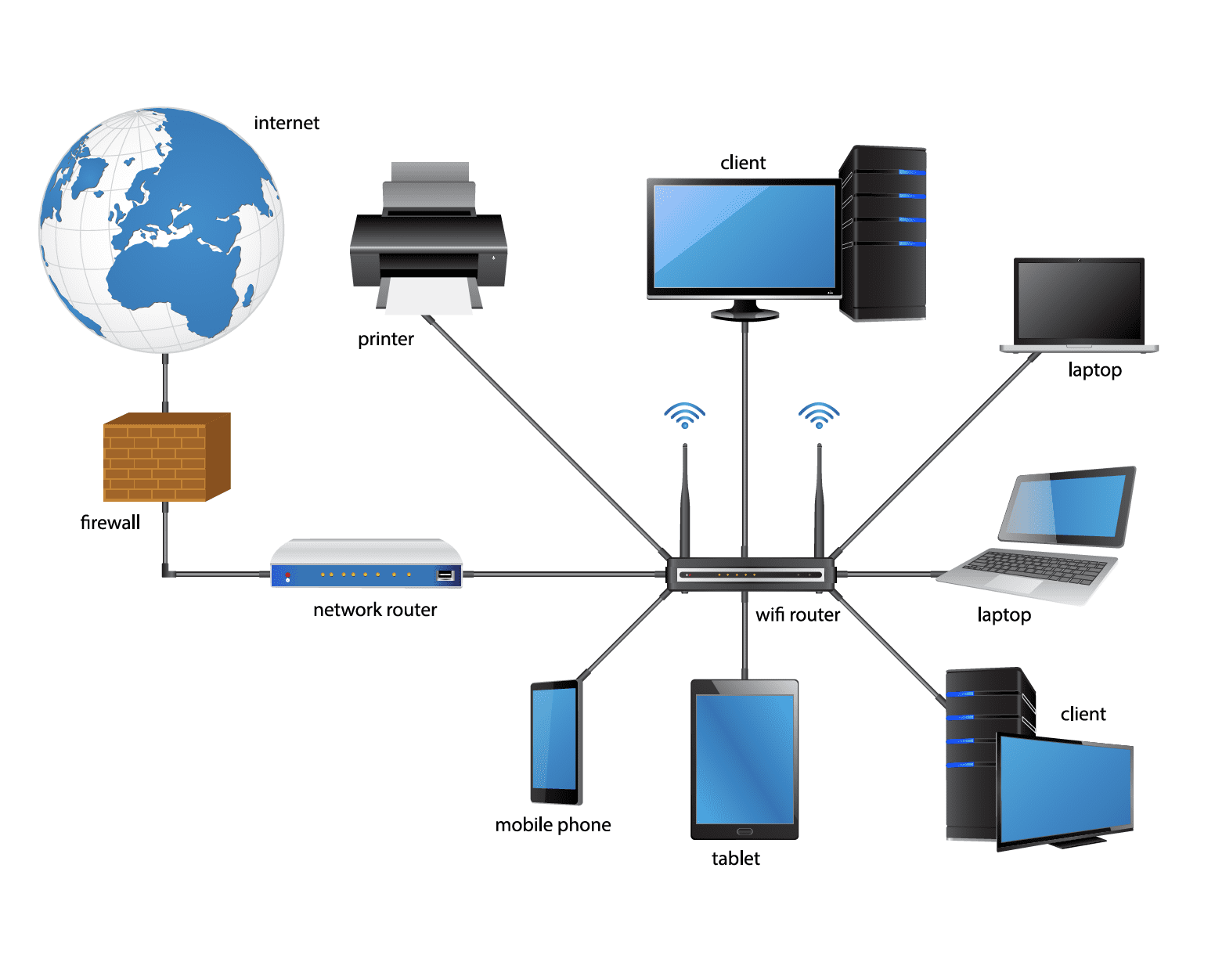
Network Diagram
Have a diagram that details your network, including all sites, major hardware, and IP addresses. This will visually represent how your systems connect and which data elements are passed between the systems.
Payment Systems
Provide details about your merchant identification, gateways, processors, and payment systems in use. This is an area many companies find complex to transfer. Leverage the vendors to support documenting this information.
Disaster Recovery and Business Continuity Plans
Document the processes used to maintain business operations in the event of a disaster or outage. In the event of a fire or hurricane, for example, detail how you communicate with owners, guests, and staff, potentially without access to all of your systems or data. If there was an Internet or network outage, provide your operating processes for maintaining standard services for all guest and owner interactions.
Prior Breaches
Provide full transparency on any data breaches that have occurred. This should include the scope of the breach, any notifications provided, and all corrective or preventative actions taken after the event occurred.
User Data
Export a list of all application users from significant systems. Provide detail on any super users and/or system administrators. Additionally, any shared accounts or service accounts should be highlighted.
Social Media
List all tools and accounts in use across your digital marketing tools. Include users and passwords.
Websites
Include a list of all owned domains, the domain registrars, and current status (active versus parked or redirected). Include relevant performance metrics that represent the level of engagement with the platform. If the platform is proprietary, provide full technology stack details along with support resources.
Channel Data
For all your sales channels (direct, web, OTA, etc.), provide the percent of revenue per channel. A full listing off all OTAs in use should be included.
Compliance Status
For PCI Compliance, present the prior four quarters of the required vulnerability scans, most recent Attestation of PCI Compliance, and inventory of all vendors with access to sensitive data, including credit card or personally identifiable information (PII).
Technology Projects
Any projects in progress, critically needed, or future planned projects should be supplied with details on the effort, the rationale, and the impact. Provide available budgetary data and timelines for these efforts.
Technology Spend
Present the total operating expense for all technology services in use, including systems, personnel, and vendors. Include the data as a percent of gross revenue. Provide historical and budgeted capital spending totals or percentages of gross revenue.
This is meant to be a guide to help VRs when selling their business. Each situation is unique and varies in complexity. There are consultants and deal brokers who are willing to help with this type of data development for those who would need that type of assistance.