Some History
While extended stays or mid-term stays (these go by many names) have been a hot topic recently, they have a rich history of helping vacation rental managers through leaner times. The most common examples are destinations that rely heavily on snowbirds in Arizona, the Gulf Coast, South Carolina, and Florida.
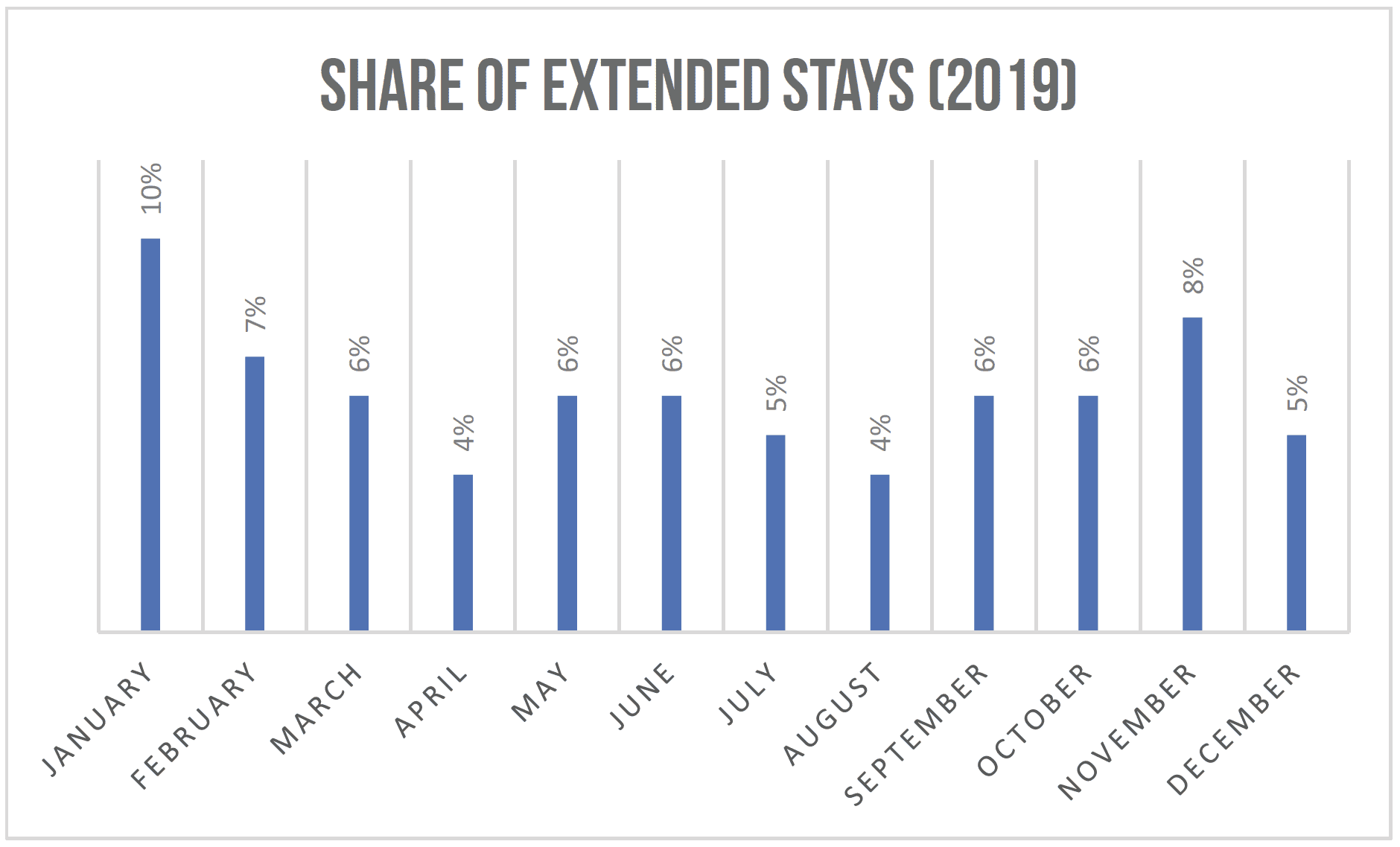
Data from a mix of different markets around the world (including beaches, ski resorts, and cities) indicate that last year, depending on the month, extended stays had 5–10 percent of the share of occupied nights. Look closer, and you’ll find that the share of extended stays tends to increase quite a bit during lean times! This is in part a supply-and-demand dynamic:
• During low seasons (or low-demand periods), managers are more willing to heavily discount the prices to get something on the books.
• Guests notice this, and the ones who have the flexibility to do so book extended stays during the low season.
We should also note that extended stays are less common in high-demand periods partly because the prices are higher, but also because with shorter bookings already in the calendar, not many facilities have consecutive available dates to take even one.
Coming Back to This Year
Coming back to present times and the buzz around extended stays, it’s not news that many destinations around the world are experiencing a low-demand period like never before. At the same time, more and more folks now have the flexibility to stay wherever they wish and work remotely. There are also other segments of demand in which the behavior has shifted toward needing longer stays, sometimes immediately. The needs might be different, but the outcome is the same, in terms of increased demand for extended stays. The data speaks for itself—the market share for extended stays in January and February (pre-pandemic) was about the same as in 2019, but since then it has increased considerably.
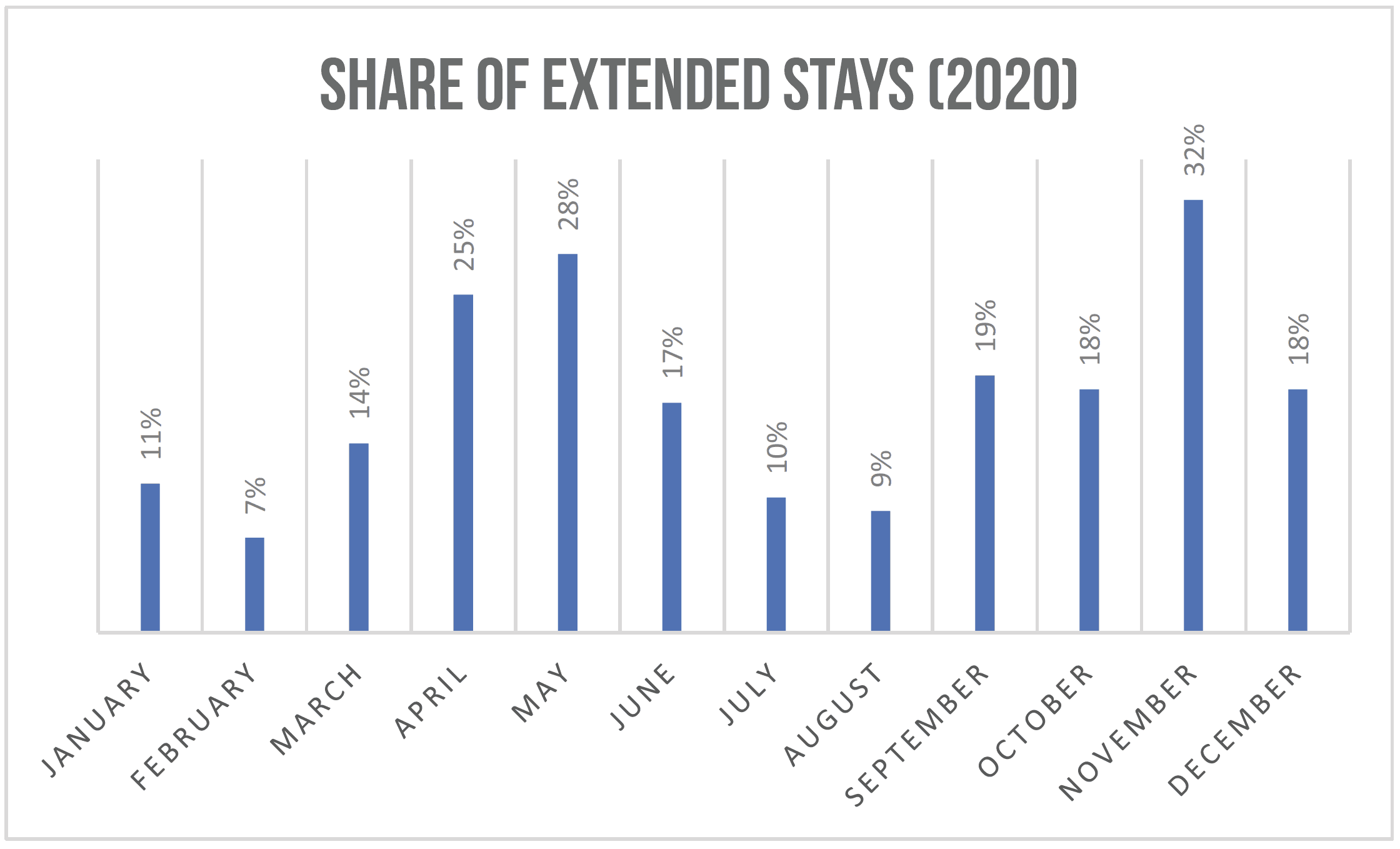
Regardless of whether the demand is from traditional snowbirds, families with remote work and school, or essential workers needing a place to stay, it’s hard to deny that extended stays play the steadying hand during low-demand periods. If you’re not already including extended stays in your revenue strategy, that might be something useful to look into. But before you do that, it’s important to understand some revenue fundamentals as well as some operational trade-offs.
Trade-Offs When Considering Extended Stays
The most important reason to consider extended stays as a revenue strategy is to reduce your revenue risk: getting an extended stay for the coming months might mean a steady revenue stream—especially if you’re in a market with weaker-than-usual demand. The revenue might not end up being as high as previous years when there was strong demand, but if it can improve what you expect to make with lower short-term demand, then that’s a win! Equally important, extended stays come with lower risk of cancellations, due to the ever-changing dynamics of the ongoing pandemic.
That said, if you’re in one of the markets where short-term booking activity is strong enough to meet occupancy goals without discounting rates heavily, extended stays might not be the right way to go. Like so many other things, this is something each manager should evaluate for themselves.
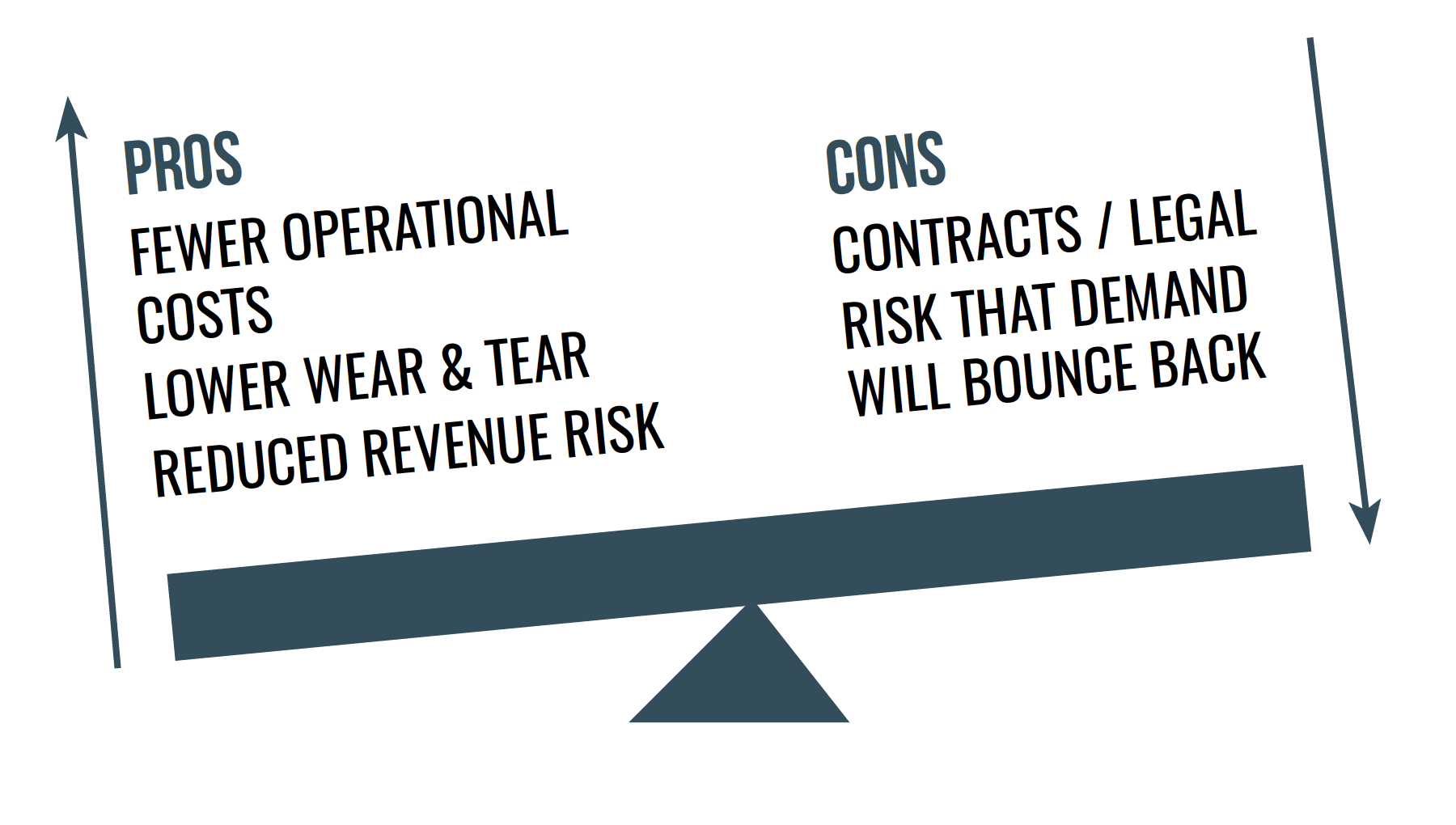 An important thing to consider: though the revenue from extended stays might be lower, the profitability might not be, because these stays have fewer operational costs than shorter stays. The wear and tear on the property also tends to be lower; guests who stay longer have some incentive to treat the property with care.
An important thing to consider: though the revenue from extended stays might be lower, the profitability might not be, because these stays have fewer operational costs than shorter stays. The wear and tear on the property also tends to be lower; guests who stay longer have some incentive to treat the property with care.
But more than anything else, it is very important to be aware of the local regulations in your market; many markets have different tenant laws for longer stays than they do for short-term stays. This can take many forms. For example, if tenant laws apply, you might need a separate permit/license for those or a different contract with the guests. Please look into this; the answer will be different, depending on the location.
Market Analysis and Distribution
If you have not been taking extended stays till now, it might be worthwhile to do some market research to find out a) if extended stays are common in your area and b) what booking channels they come through.
For example, Tucson, Arizona, is a popular destination for snowbirds and shows fairly strong demand for longer stays during winter months. Galveston, Texas, conversely, is a popular weekend destination a short drive from Houston. Looking at the mix of bookings in forward-looking market data, it’s clear that a lot of snowbirds have already been booking extended stays through spring of 2021 in Tucson. On the other hand, in Galveston there is hardly any demand for extended stays right now; most bookings come for shorter stays over the weekend.
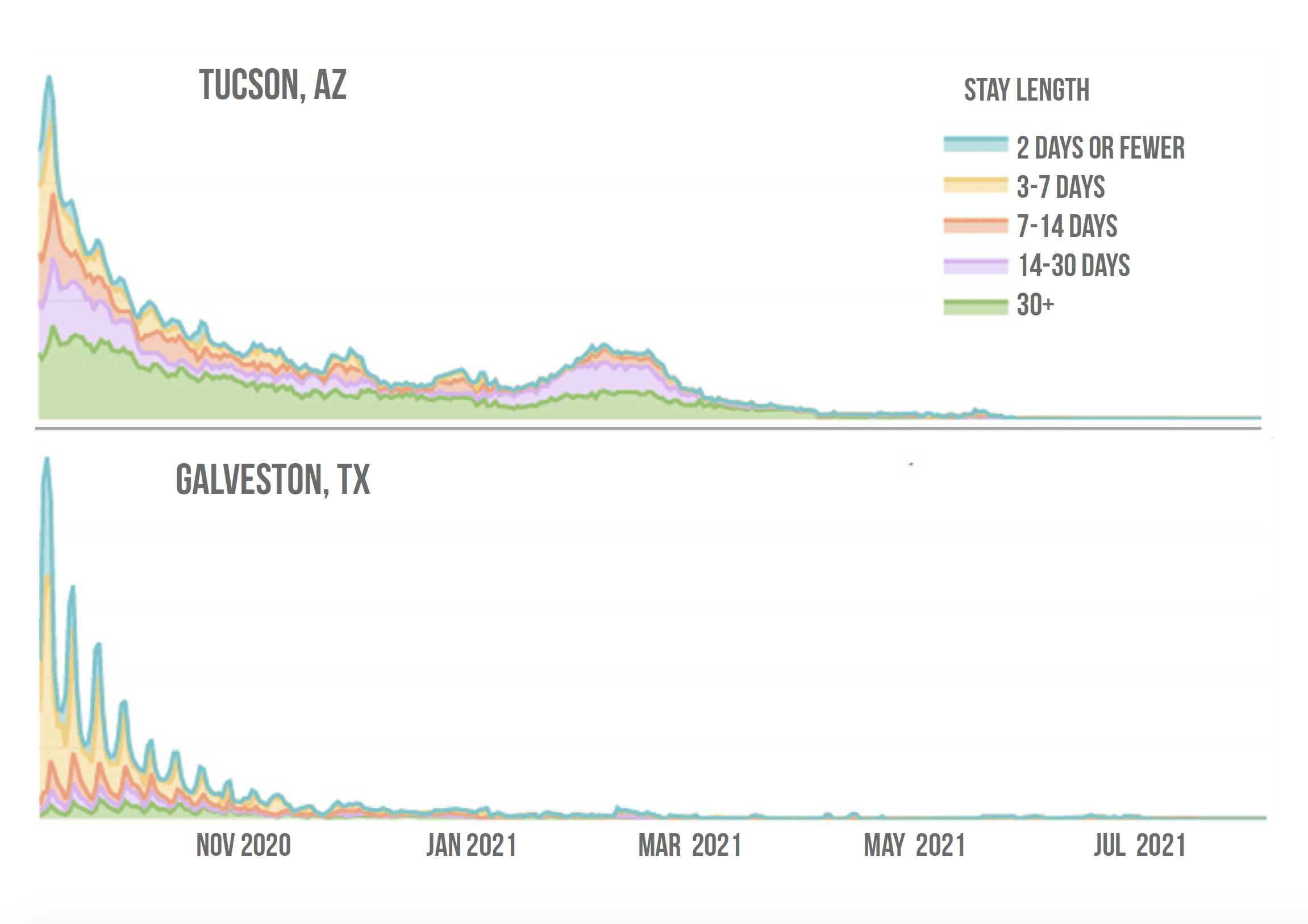
It’s not just important to know if your market has a demand for extended stays; you will also want to know how and where those bookings are made. Major OTAs like VRBO, Airbnb, and Booking.com have added focus on extended stays recently. Many markets get demand from boutique channels like Furnished Finder or Traveling Nurse Housing, and these might be worth exploring.
Marketing to repeat guests is always a great way to test the waters with guests you trust. It might also be a way to see if you can generate that demand even if market data sources fail to show strong indicators for it in your broader market just yet.
Revenue Risk and Profitability: Discounting Extended Stays
Let’s say you’ve thought through the above, and the idea of extended stays checks out on multiple fronts. Before diving in, it makes sense to do some back-of-the-napkin math.
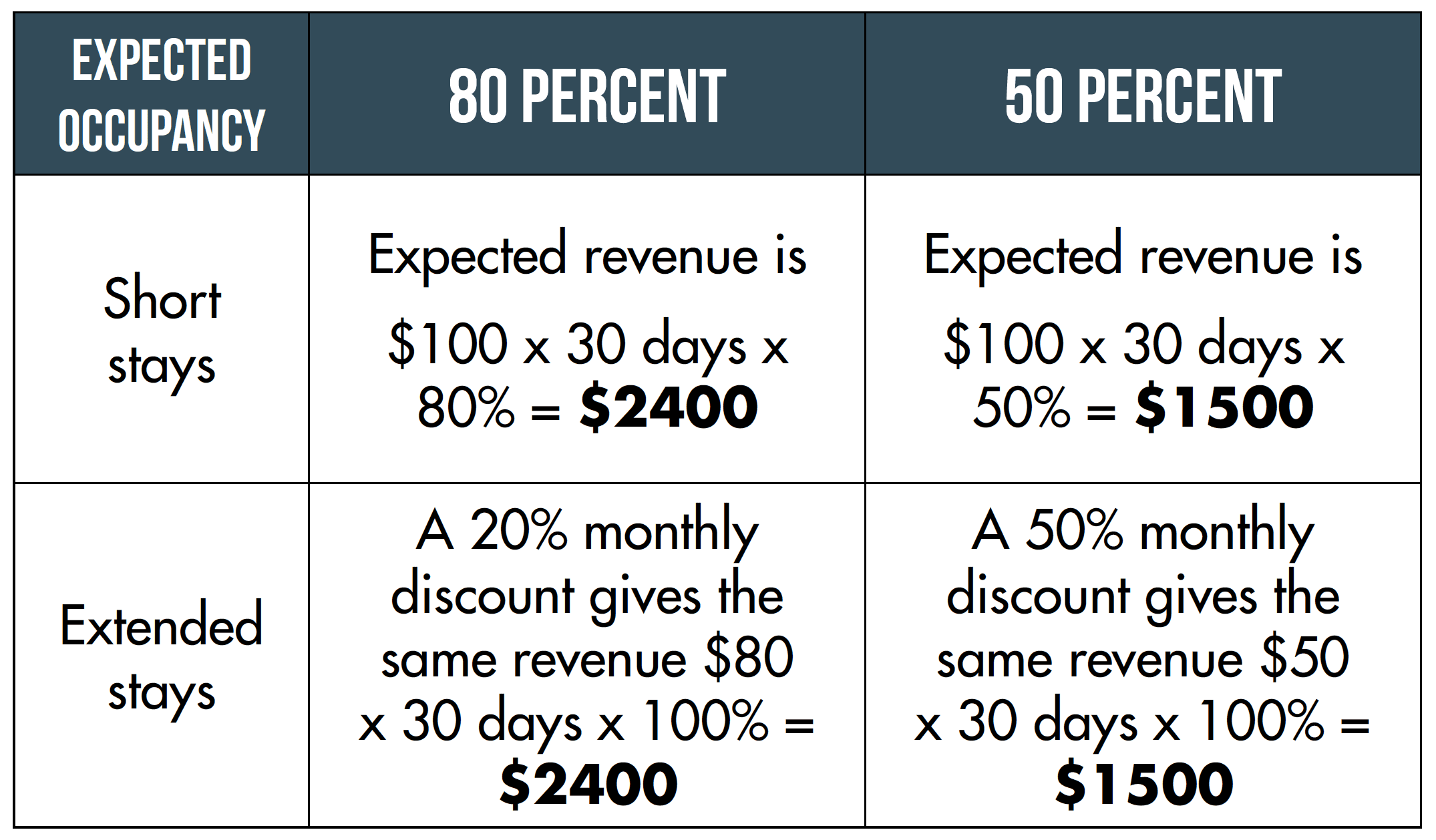
Let’s run through a couple of hypothetical scenarios to help understand this better. For easier math, let’s say you have a property that, on average, sells for $100/night during the upcoming season (some nights might be higher, some lower—we’re looking at the average here). It’s tough to forecast anything right now, but based on recent history, let’s say you have some sense of how booked you expect to be in the coming months from short-term rentals.
Expect to be 80 percent booked in the coming months: If you try and attract monthly stays with a 20 percent monthly discount, you’ll achieve about the same revenue.
Expect to be 50 percent booked in the coming months: You can discount much higher (up to 50 percent) and still make the same revenue!
 A few important caveats here:
A few important caveats here:
1) Though a large discount means you might make the same revenue, it doesn’t mean you should discount all the way up. The amount you discount longer stays should depend on what kind of demand exists for those extended stays and what you’re comfortable with. You might get better revenue with a smaller discount that still makes your property attractive for longer stays.
2) Giving monthly discounts doesn’t mean that you will get a monthly booking—it just means that it increases your chances of getting one.
3) If you decide to increase or decrease your nightly rates to respond to demand, this might mean the expected occupancy will also change. You might have to revisit your monthly discounts in such a case.
4) Many platforms and distribution channels don’t allow for different monthly discounts each month. If you’re in a seasonal market, you might need to find ways not to have heavy monthly discounts apply for the high season next year (there are a few possibilities, such as using a maximum LOS for high-demand periods or setting monthly discounts to only apply to certain months, if possible).
Finally, in this example we tried to find the highest monthly discount you should apply purely from a revenue perspective. If there are other considerations (peace of mind, fewer operations, reduced risk), you’ll have to think about how you value them. With an extended stay, you’re also losing the chance of getting those higher-value bookings when demand picks up again.
Segmenting with Minimum-Stay Restrictions
One of the more advanced techniques used by managers who know their market and portfolio really well is to actively ensure that they don’t get short bookings when there’s a better chance of getting longer bookings and better overall revenue.
As an example, consider a slow month (say February) that gets two kinds of bookings:
• Shorter bookings around Valentine’s Day
• Extended stays from snowbirds
The catch? If you get one of those to book, you can’t get the other. And while the shorter booking comes at a good nightly rate, the extended stay fetches more revenue, given how low February occupancy gets in this hypothetical market.
What if you could find a way to get that extended stay to book, while also having the option to fall back on the shorter Valentine’s Day booking if it doesn’t come through? This would require you to find some way to segment these guests; one of the most common ways is using the booking window.
Many folks who book the shorter stays tend to book them last-minute with a short booking window, but some might plan ahead. If you get that rare far-out booking around Valentine’s Day, there’s no opportunity left to take a longer booking around it.
Some managers use the following strategy instead:
1) Study when most of the bookings for Valentine’s Day start coming in. Say 90 percent of those come after January 1 (you can use your own data from past years or forward-looking market data).
2) Till January 1, keep the minimum stay for February higher— you’re effectively hoping for an extended stay and “rejecting” 10 percent of the Valentine’s Day demand that books early.
3) If you’re still not booked with the extended stay when the new year rolls over, drop the minimum stay requirement to cater to the remaining 90 percent of the Valentine’s Day demand.
The booking windows and risk tolerance in this strategy will vary by location and manager, but the overall strategy works well. This is also something you can experiment with if you manage multiple properties.
Do remember not to do this during high season or during periods when the booking window is long, or you’ll be “rejecting” a larger portion of the demand for the shorter bookings, which might not be beneficial.
Balancing Short-Term Rentals vs. Extended Stays: Adjacent and Orphan Nights
Suppose you get a few extended stays on your calendar. Depending on the season, and whether or not those extended stays resulted in awkward gaps in your calendar, filling those gaps could be challenging. There are a few reasons for this:
• Days right next to an existing booking are usually harder to fill: someone should want to book a stay starting or ending right about where the existing reservations are.
• Days between two bookings get even harder: anyone who wants to book longer stays won’t even find your property in a search.
Effectively, the demand for those dates is lower. In such cases, it becomes even more important to be nimble with your prices and min-stays.
The minimum-stay (min-stay) requirement pose a “hard” constraint: if you have a six- or two-night gap and a seven-night min-stay for those dates, there’s no way you’ll get booked (or even show up on a search in OTAs and your direct booking website). You (and property owners) might be okay filling longer gaps of three to six nights but don’t really want one- or two-night bookings, so for contractual reasons, min-stay will ensure those single-night guests don’t book, even when there’s a gap.
If there’s no contractual reason to avoid shorter stays, managers often use one of these two pricing strategies for a more desired outcome on orphan/adjacent nights:
• Increase the price: this one is for operational efficiency. Sometimes you don’t want to fill short gaps unless the price you get is much higher than normal, to make it worth it, or on adjacent days, you might want to avoid back-to-back reservations unless the rate for those nights is very high. In either case, increasing the price will help.
• Decrease the price: this is usually done for improved revenue. Gaps and adjacent days can be harder to fill during low-demand periods, so incentivizing bookings on those days can help. They will increase operational load (which should be low to start with during low season) but can improve revenue and profitability.
Conclusion
Revenue management is a complicated process—there are so many variables that come into play: what the market is doing, what your operations can support, and what the owners prefer. Throwing extended stays into the mix might seem daunting, but when incentivized well, so as to not cannibalize revenue from short-term stays, this strategy can result in a win-win situation for both you and the owners. The strategies mentioned here might seem cumbersome but can be managed with a hands-on approach, automation, or a mix of both. If you manage many properties, these activities might be worth considering in some part of your portfolio.



























 An important thing to consider: though the revenue from extended stays might be lower, the profitability might not be, because these stays have fewer operational costs than shorter stays. The wear and tear on the property also tends to be lower; guests who stay longer have some incentive to treat the property with care.
An important thing to consider: though the revenue from extended stays might be lower, the profitability might not be, because these stays have fewer operational costs than shorter stays. The wear and tear on the property also tends to be lower; guests who stay longer have some incentive to treat the property with care.
 A few important caveats here:
A few important caveats here:
 Dynamic pricing software has also become popular in the vacation rental industry over the past few years as managers look to gain competitive pricing advantages in their market. Dynamic pricing tools are the closest thing that the vacation rental industry currently has to a revenue management system, something that hotels and airlines use alongside a PMS to manage all the strategic levers available to revenue managers. These systems take a lot of the manual work out of pricing and reacting to market shifts in supply and demand, allowing property managers more time to focus elsewhere. Most property managers using a dynamic pricing tool are also able to use custom pricing settings and features to maintain a more advanced strategy in a more efficient manner.
Dynamic pricing software has also become popular in the vacation rental industry over the past few years as managers look to gain competitive pricing advantages in their market. Dynamic pricing tools are the closest thing that the vacation rental industry currently has to a revenue management system, something that hotels and airlines use alongside a PMS to manage all the strategic levers available to revenue managers. These systems take a lot of the manual work out of pricing and reacting to market shifts in supply and demand, allowing property managers more time to focus elsewhere. Most property managers using a dynamic pricing tool are also able to use custom pricing settings and features to maintain a more advanced strategy in a more efficient manner.
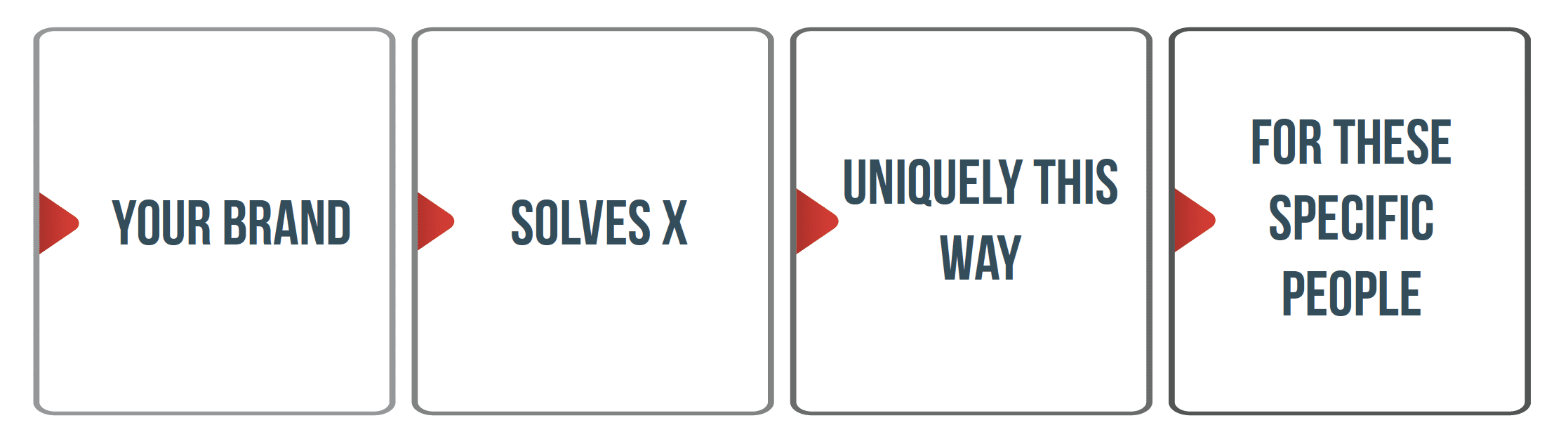 However, filling in the formula with your details is not so easy. In fact, most people get stuck on “uniquely this way” and “for these specific people.”
However, filling in the formula with your details is not so easy. In fact, most people get stuck on “uniquely this way” and “for these specific people.”
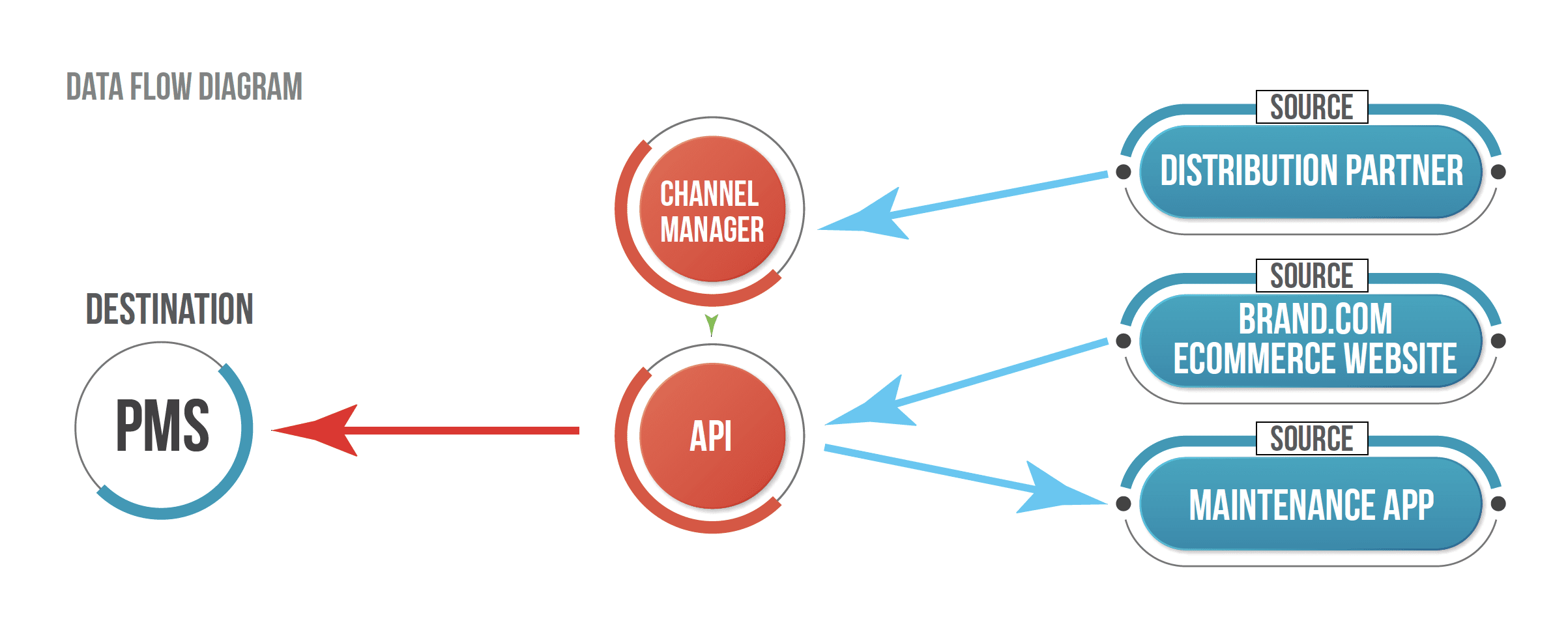


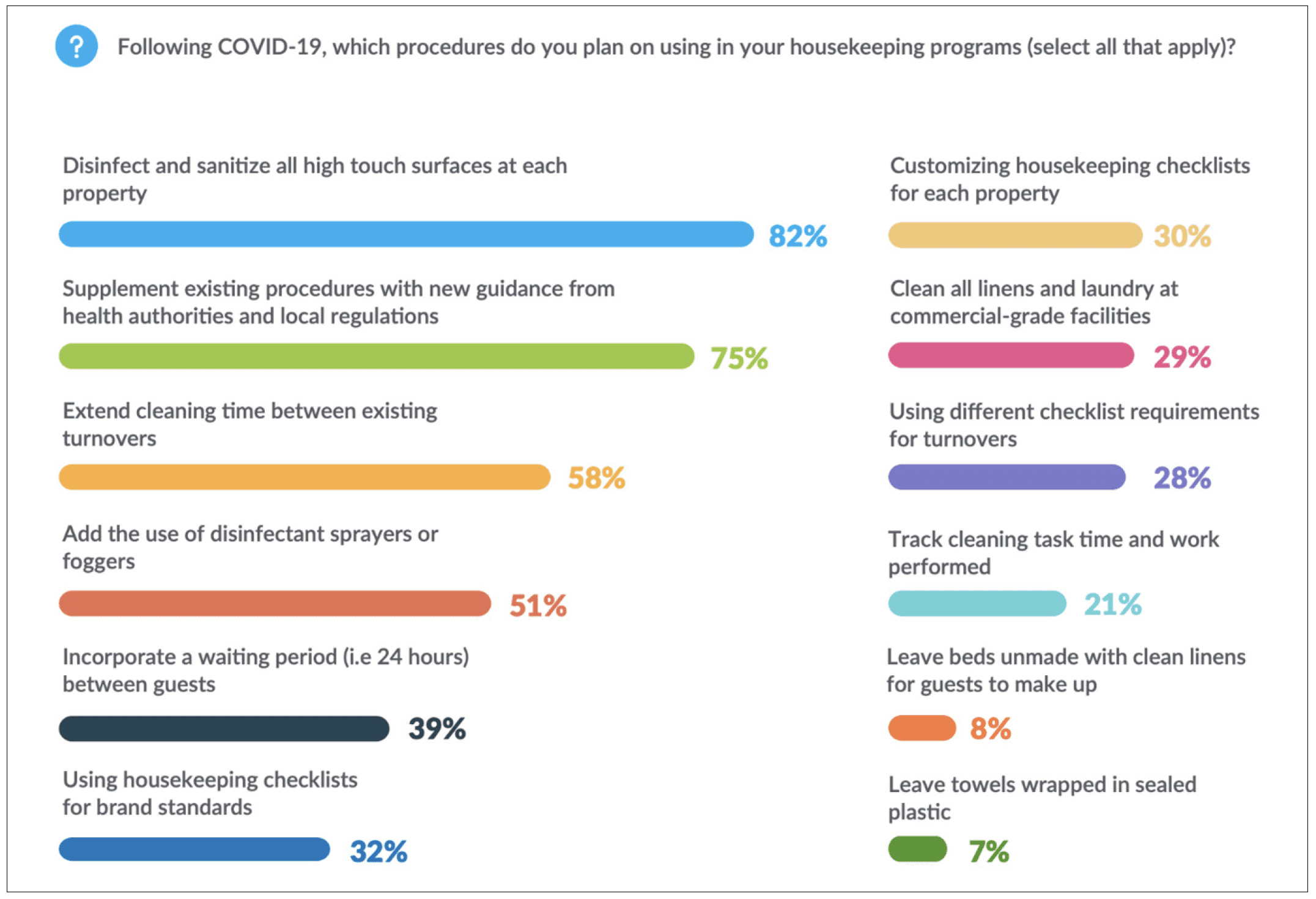
 In fact, more than 42 percent of professional managers we surveyed are manually plugging gaps in property care by scheduling tasks from reservation reports, using paper checklists to perform quality assurance, and communicating internally through ad hoc systems, phone calls, and text threads. Another 40 percent are using a combination of tools which include their PMS systems, and workarounds that increase the likelihood that work will fall through the cracks.
In fact, more than 42 percent of professional managers we surveyed are manually plugging gaps in property care by scheduling tasks from reservation reports, using paper checklists to perform quality assurance, and communicating internally through ad hoc systems, phone calls, and text threads. Another 40 percent are using a combination of tools which include their PMS systems, and workarounds that increase the likelihood that work will fall through the cracks.

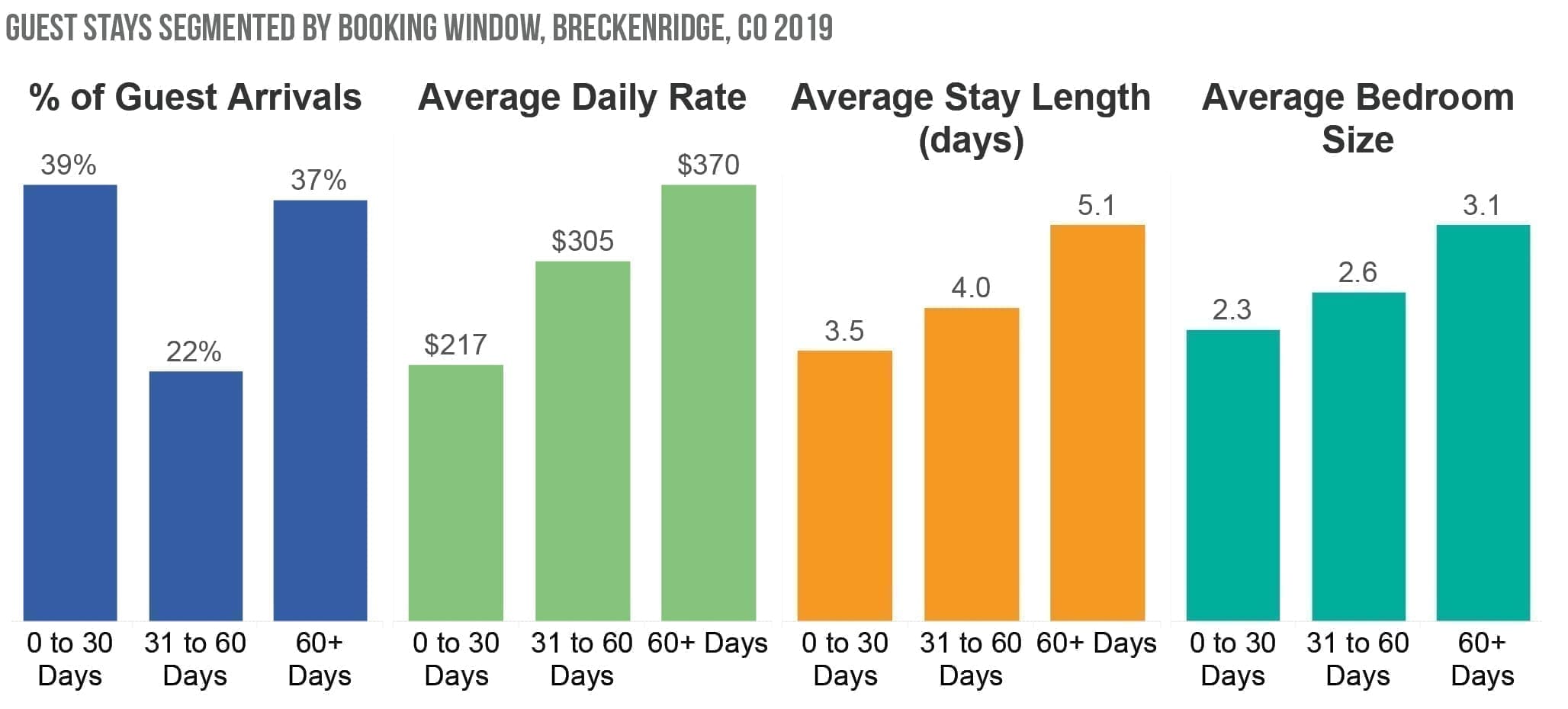
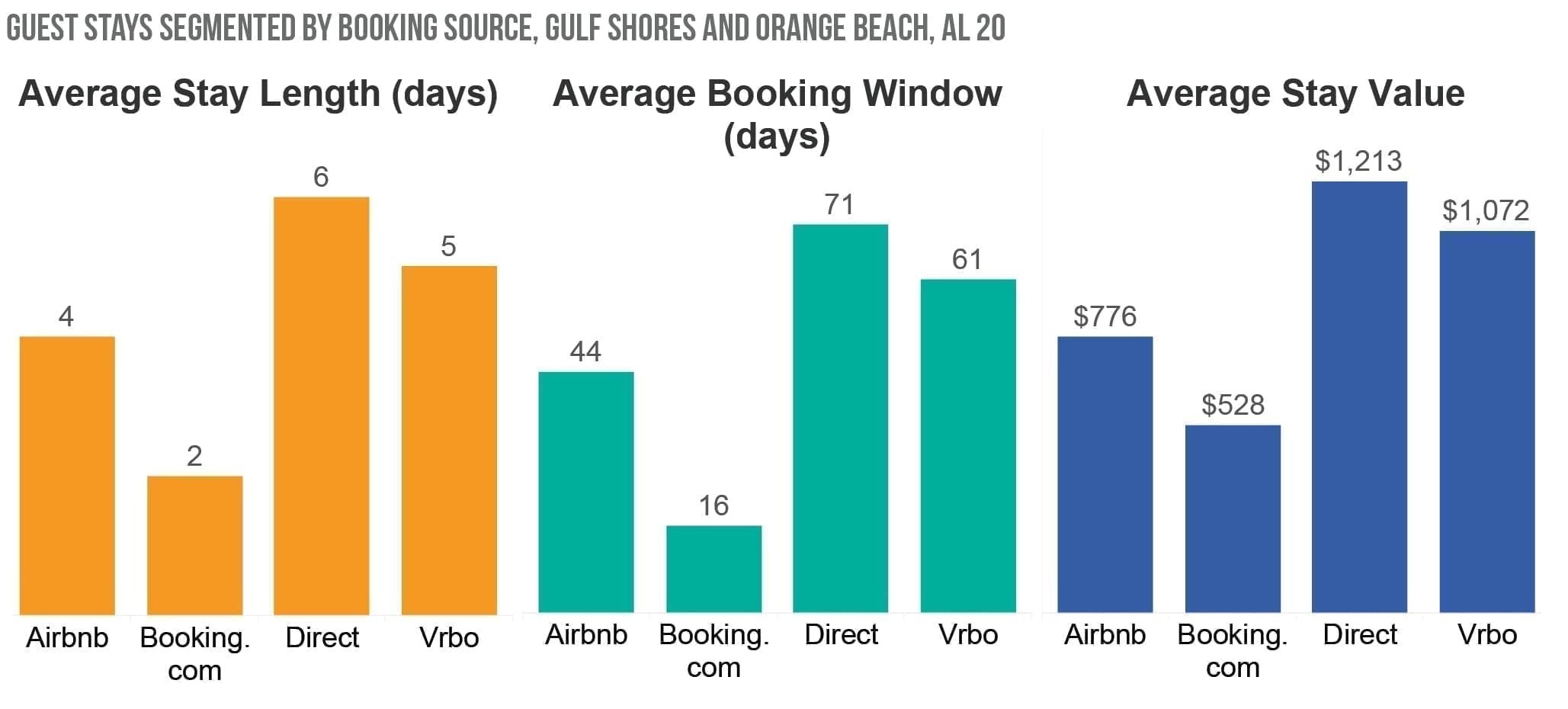
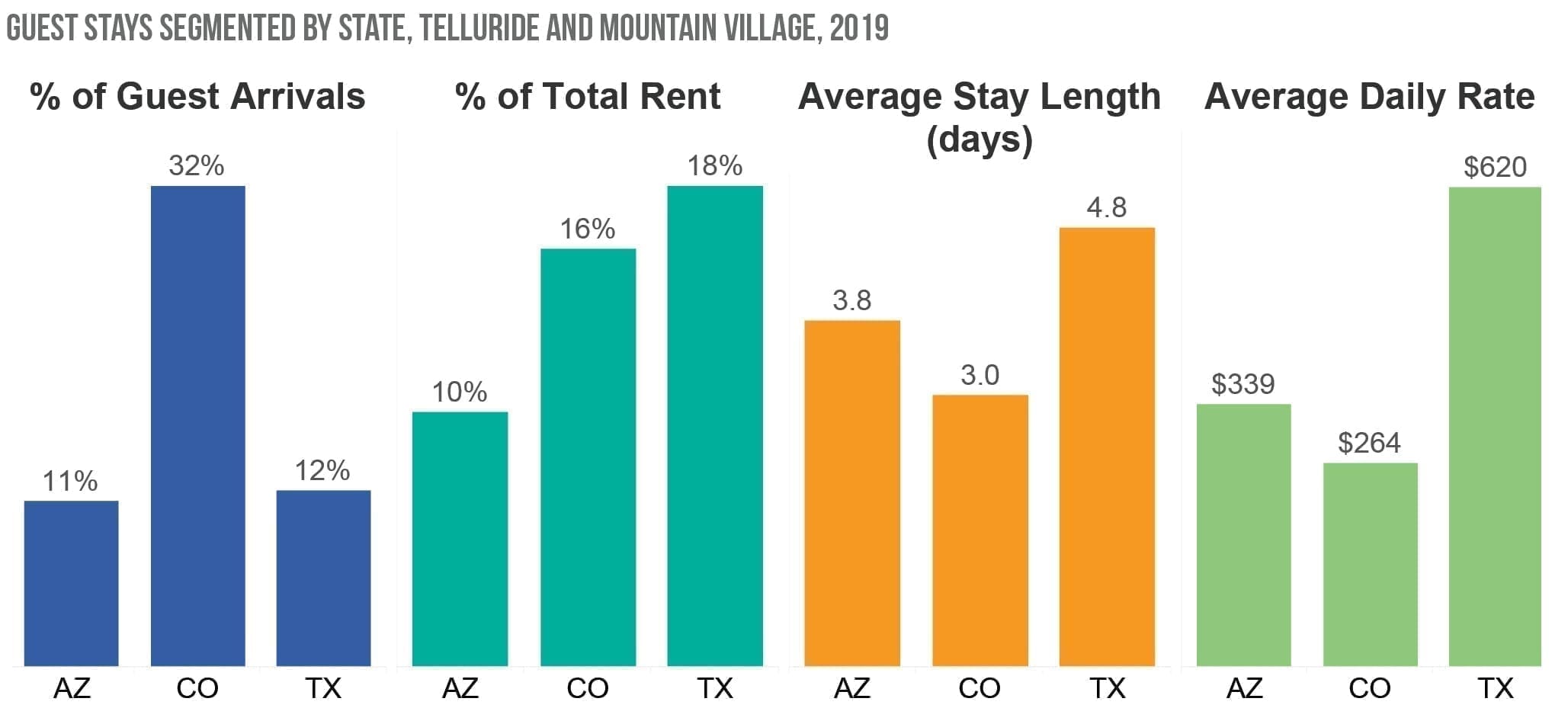
 In contrast, during the summer, 26 percent of guests arrived after booking an average of 78 days before arrival, and they stayed for an average of eight days.
In contrast, during the summer, 26 percent of guests arrived after booking an average of 78 days before arrival, and they stayed for an average of eight days.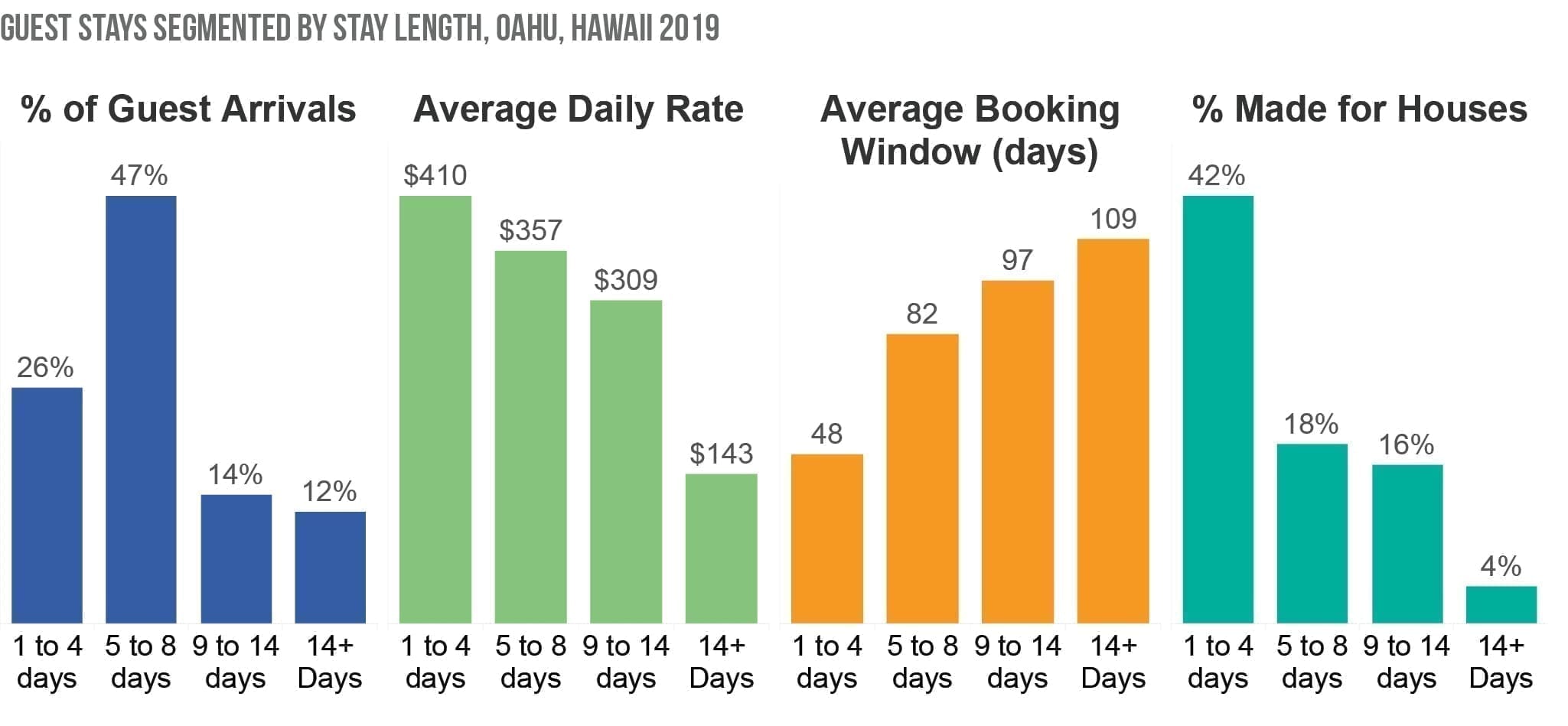





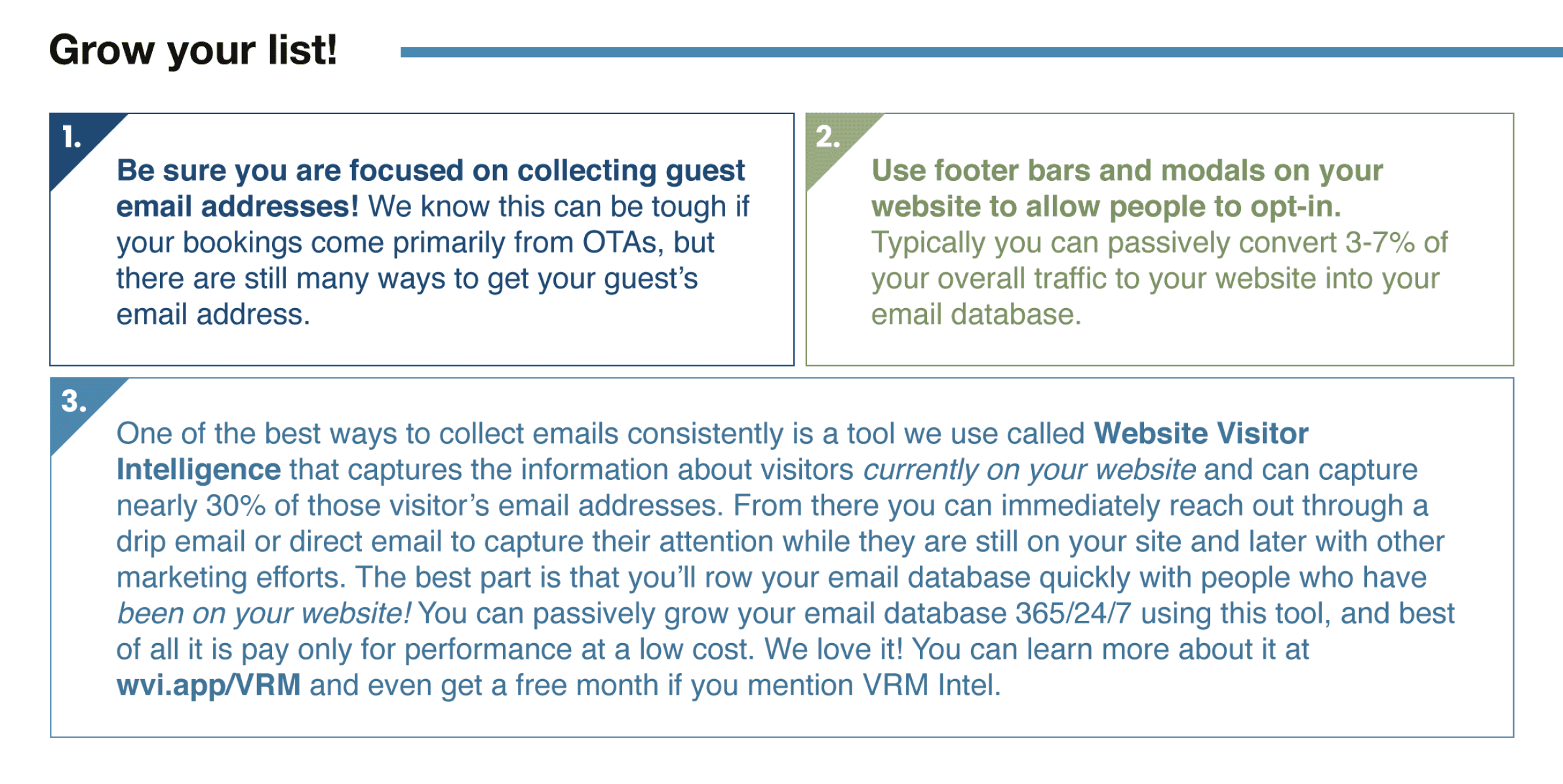
 A high-quality email database is pure gold on any day, but even more so when you need to save cash. Email should be one of your lowest acquisition costs for direct bookings and one of the highest converting marketing assets. When those two variables meet, you can generate huge revenue returns with very low expenses.
A high-quality email database is pure gold on any day, but even more so when you need to save cash. Email should be one of your lowest acquisition costs for direct bookings and one of the highest converting marketing assets. When those two variables meet, you can generate huge revenue returns with very low expenses.